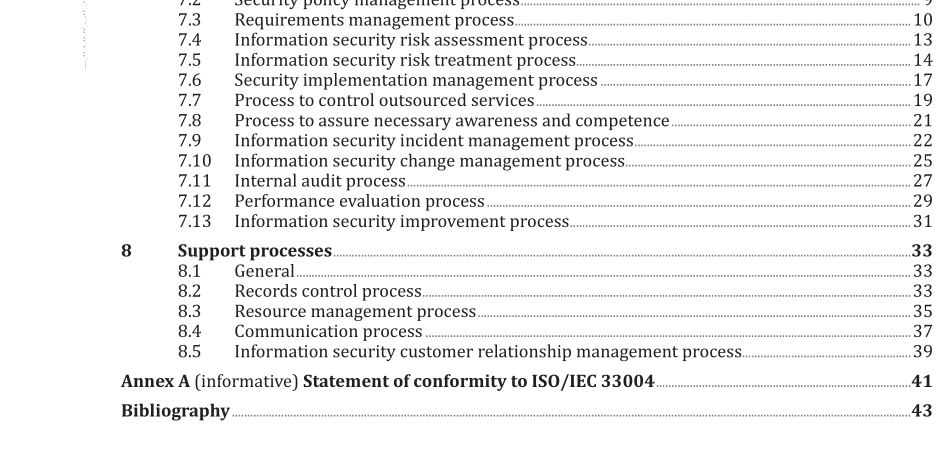
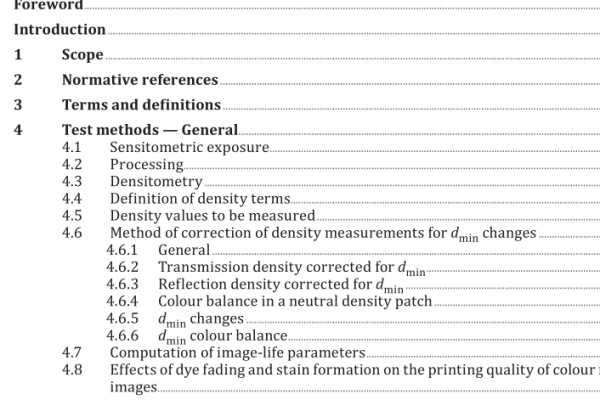
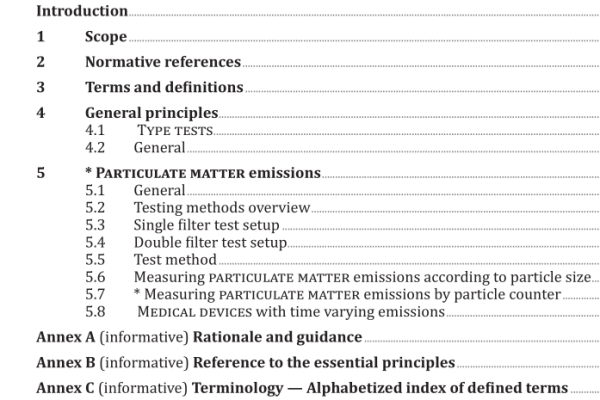
ISO IEC TS 27022:2021 pdf download – Information technology — Guidance on information security management system processes.
Key to satisfying the ISMS objectives is an up-to-date understanding of the needs and expectations of interested parties relevant to information security and the ISMS. This should be realized within the requirements management process, which should identify legal, statutory, regulatory and contractual requirements for the risk assessment process, the internal audit process and the process to control outsourced processes. In the risk assessment process, risks should be identified, analysed and evaluated. The results of this process should be documented and the evaluated risks captured in a list of prioritized risks with risk owners, which should be input for the communication process and the information security risk treatment process. In the information security risk treatment process, risk treatment options should be identified and selected, and control objectives/controls should be determined necessary for the chosen risk treatment options. The results of this process should be lists with determined controls and control objectives, a risk treatment plan including acceptance of residual risks, a control implementation plan and requests for changes for the information security change management process, which are used as input in various ISMS processes. The security implementation management process should be the process to initiate and verify the implementation of the risk treatment plan and necessary changes. As services are outsourced, these services need to be determined and controlled, which should be realized within the process to control outsourced services. Within the information security awareness process, an information security awareness, training and education program should be developed and implemented to ensure that all personnel receive the necessary security training and/or education. The information security incident management process should be for detecting, reporting, assessing, responding to, dealing with and learning from information security incidents. The results of this process are identified incidents, which should be used in various ISMS processes including the information security change management process and the process to ensure necessary awareness and competence. The implementation of controls always constitutes changes, which should be managed within a general change management process of the implementing organization or – if the change focuses on an ISMS element – within the information security change management process. The information security change management process is the process to control changes of ISMS elements and review the consequences of unintended changes. This process only focusses on change management of the ISMS. The results of this process should be necessary changes (for records control process), proposed and necessary changes as well as results of changes (for and from risk assessment process), initiation of risk assessment when significant changes are proposed or occur, and the results of changes to information security incident management process, as that process initiated them. The performance evaluation process should contain monitoring, measurement, analysis and evaluation of two main criteria. First, the performance of the security controls and second the performance of the ISMS processes. Performance measurement differs from performance audit (within the internal audit process where effectiveness and efficiency of the ISMS and implemented controls are audited), which should be performed independently. Results from the performance evaluation process, the internal audit process as well as results from the service provider audits from the process to control outsourced services should be used to improve effectiveness, efficiency, suitability and adequacy of the ISMS and the controls. This should be realized within the information security improvement process. Within the records control process information determined to be necessary for the effectiveness and/or the demonstration/provision of documented evidence of the effectiveness of the ISMS should be identified, created, updated and controlled.
ISO IEC TS 27022:2021 pdf download – Information technology — Guidance on information security management system processes